In my last blog post I described how the TIGER / MATE programs classified battles (in computer science terms ‘objects’) based on attributes and that anchored or unanchored flanks was one such attribute. After demonstrating the algorithm for calculating the presence or absence of anchored flanks we saw how the envelopment and turning tactical maneuvers were implemented. In this blog post we will look at another attribute: restricted avenues of attack and restricted avenues of retreat.

The only avenue of retreat from the Battle of First Bull Run back to Washington was over a narrow Stone Bridge. When a wagon overturned panic ensued. Library of Congress.
One classic example of a restricted avenue of retreat was the narrow stone bridge crossing Cub Run Creek which was the only eastern exit from the First Bull Run battlefield. The entire Union army would have to pass over this bridge as it fell back on Washington, D.C. When artillery fire caused a wagon to overturn and block the bridge, panic ensued.

At the battle of Antietam Burnside tried to force his entire corps over a narrow bridge to attack a Confederate position on the hill directly above. The bridge was famously carried by the 51st New York Infantry and 51st Pennsylvania Infantry who demanded restoration of their whiskey rations in return for this daring charge. From the original Edwin Forbes drawing. Click to enlarge.
Burnside’s Bridge at the battle of Antietam is a famous example of a restricted avenue of attack. Burnside was unaware that Snavely Ford was only 1.4 miles south of the stone bridge and allowed a back door into the Confederate position. Consequently, he continued to throw his corps across the bridge with disastrous results.
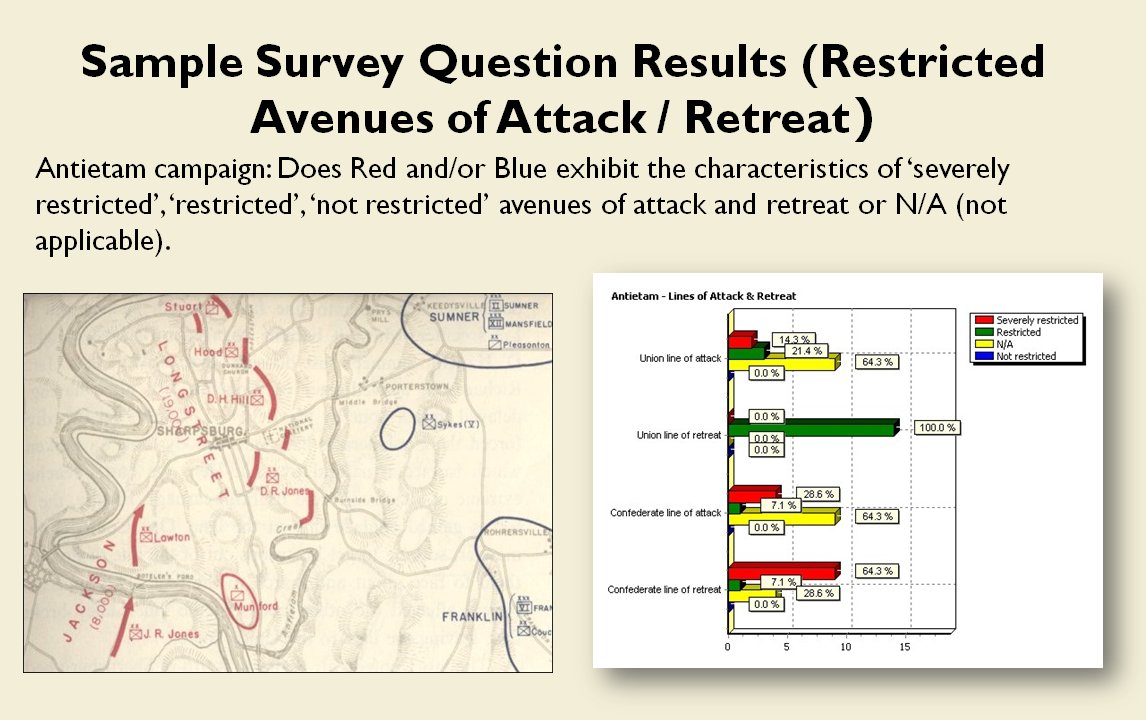
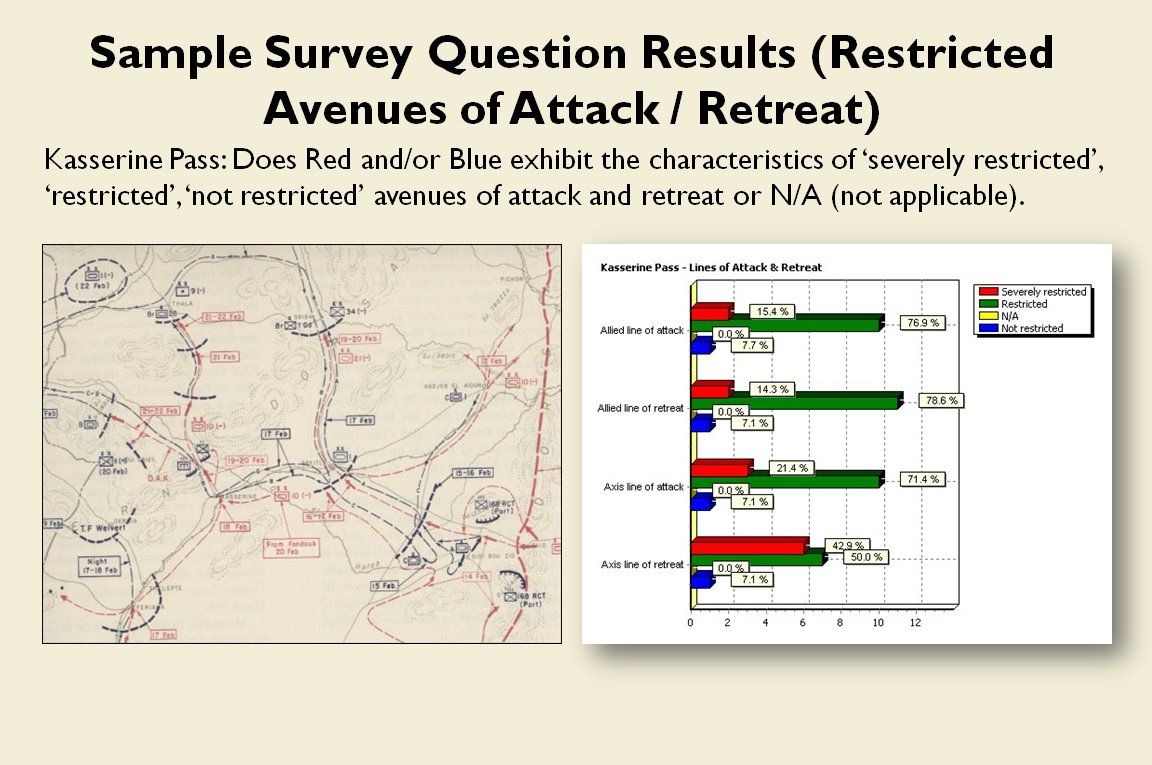
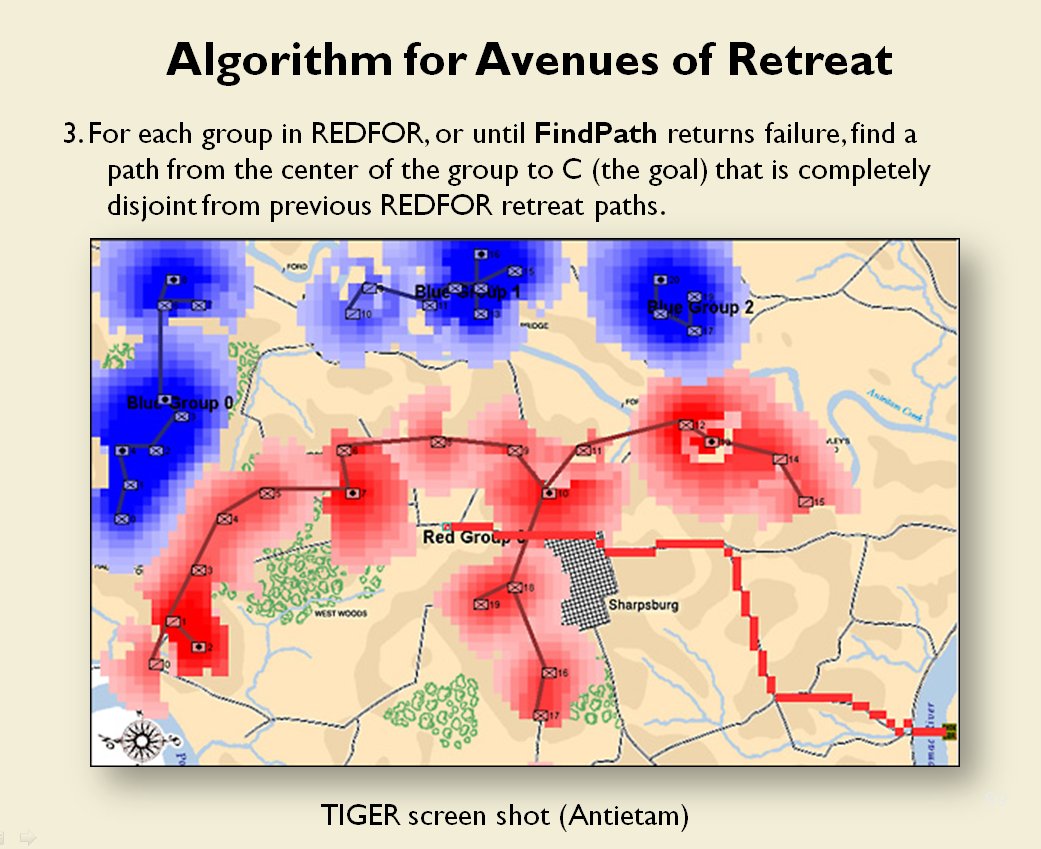
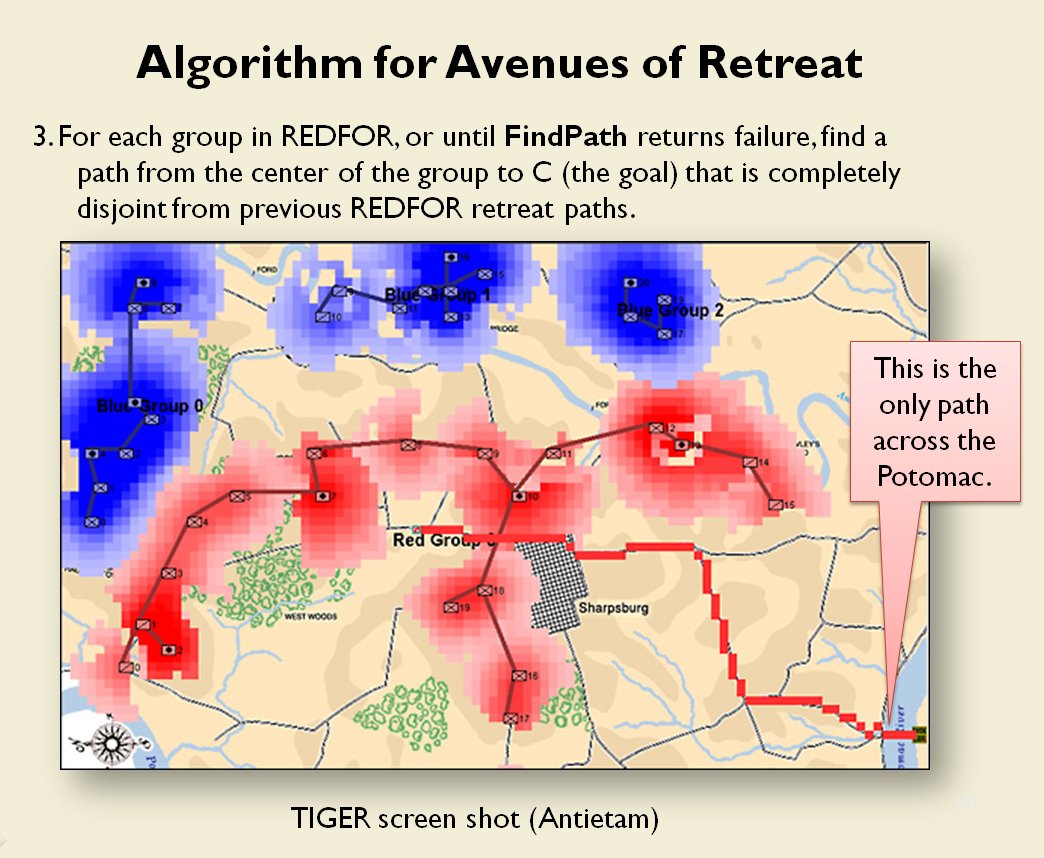
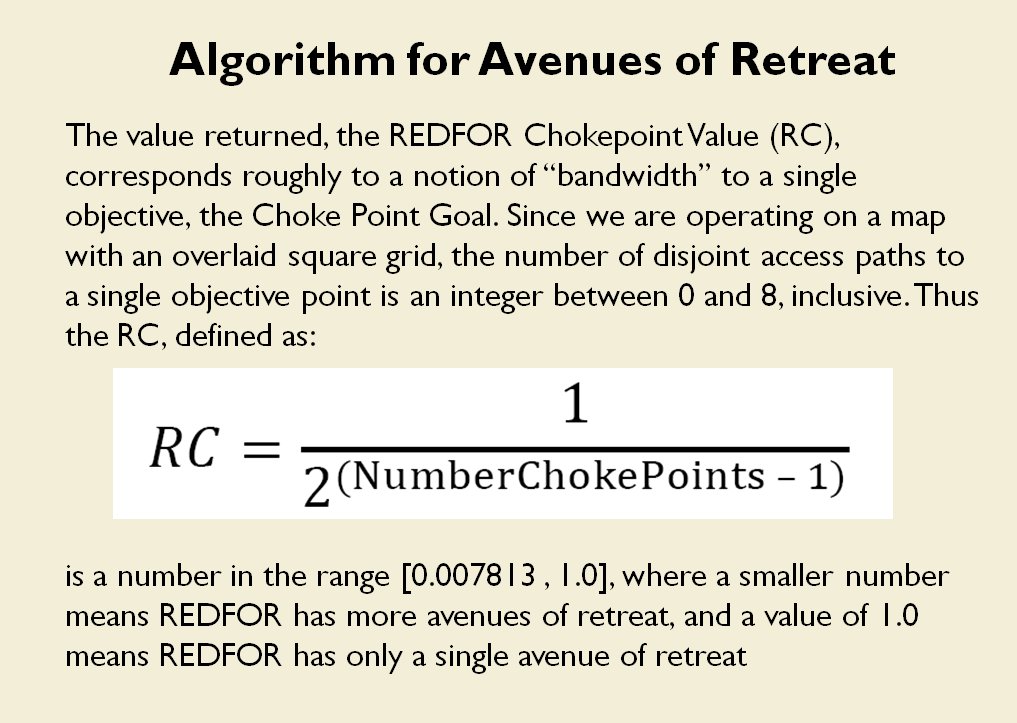
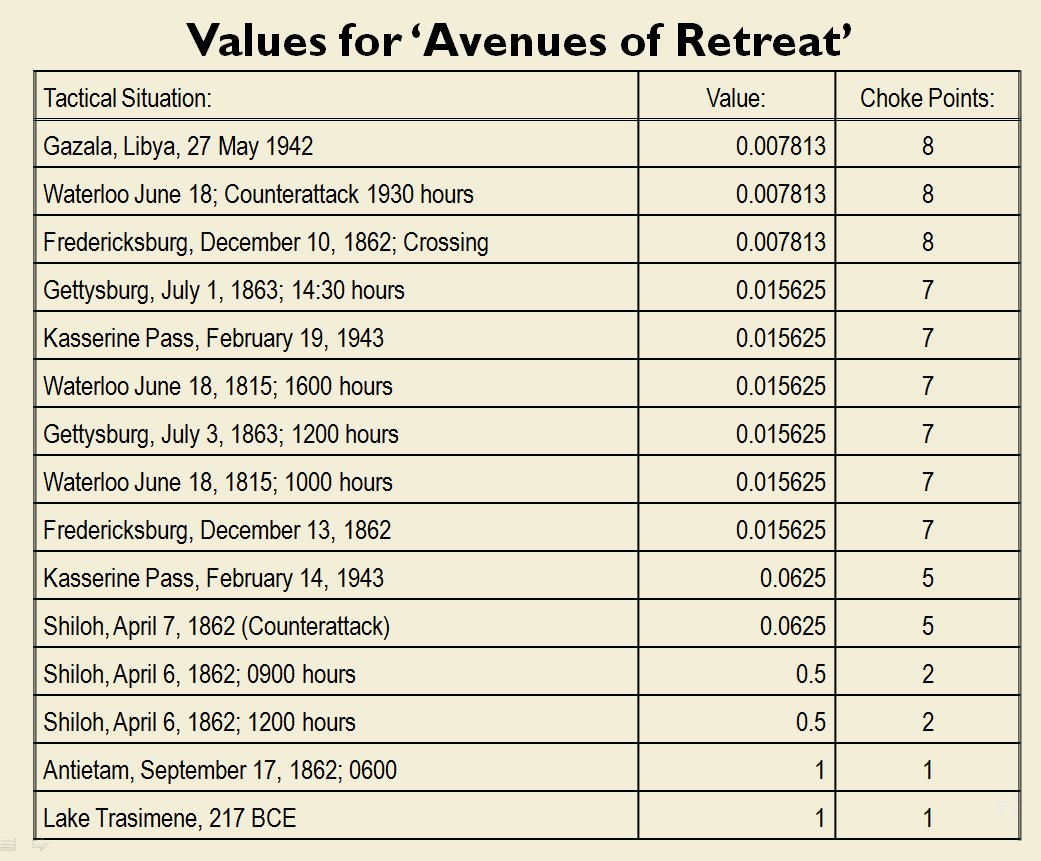
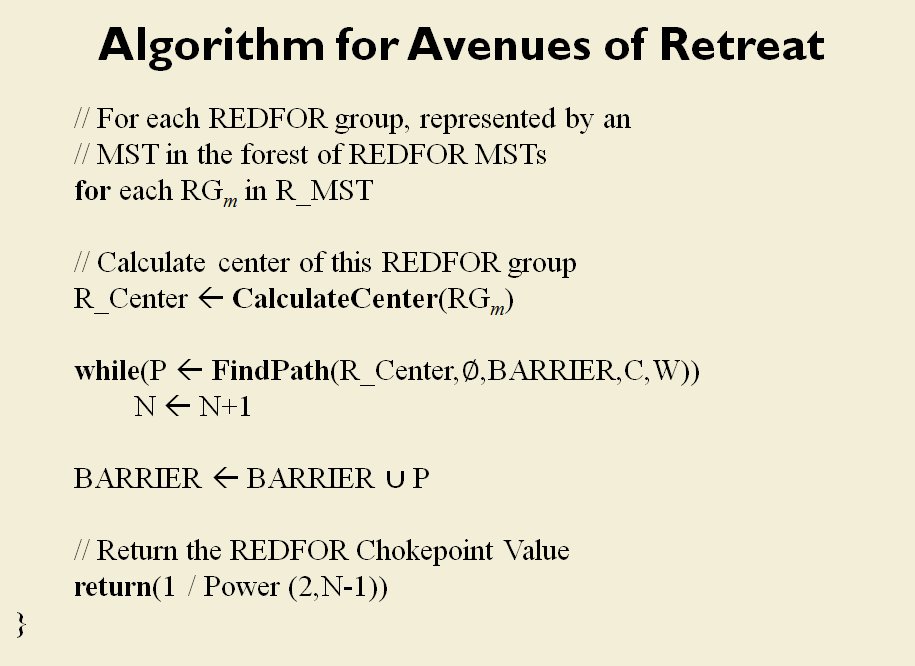
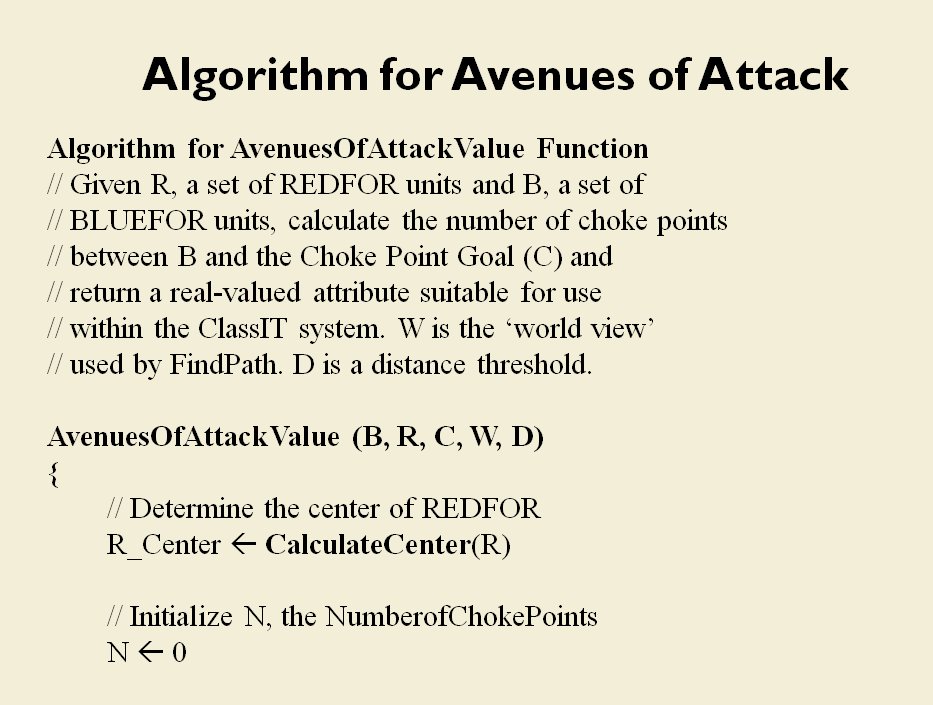
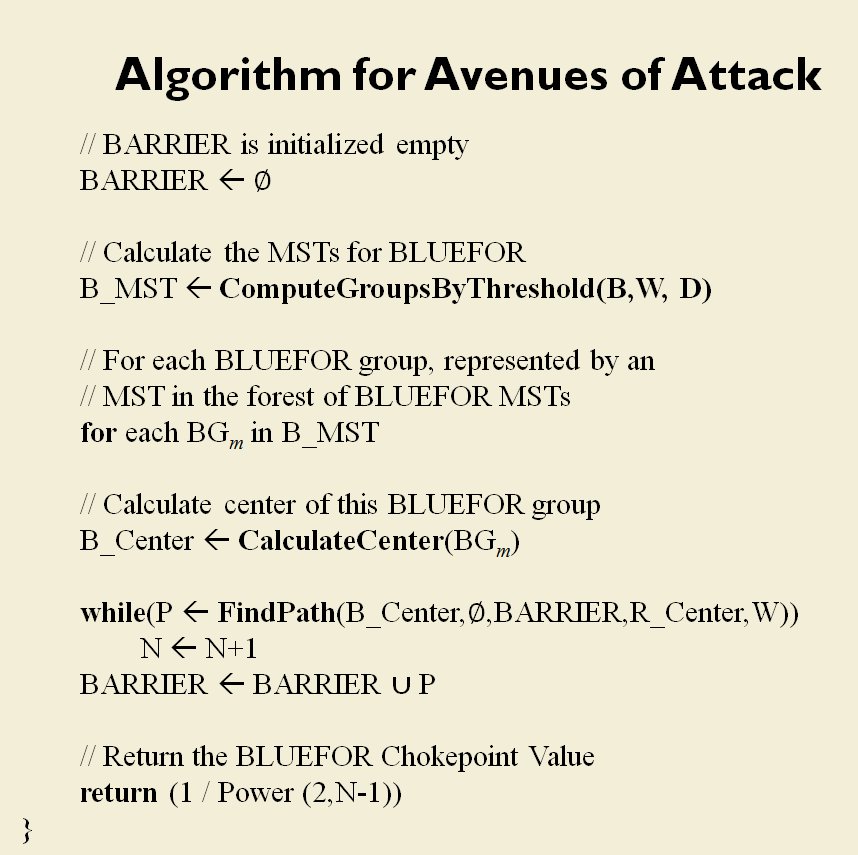
How to determine if there is a restricted line of attack or a restricted line of retreat on a battlefield
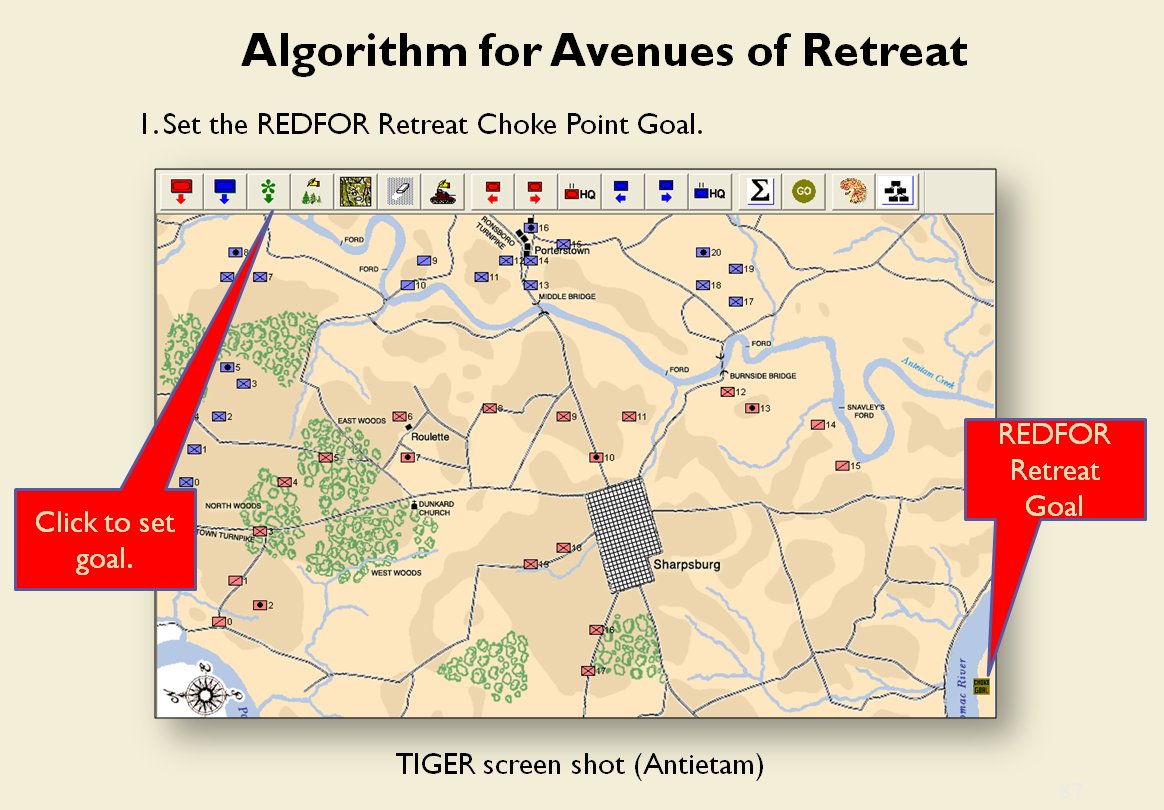
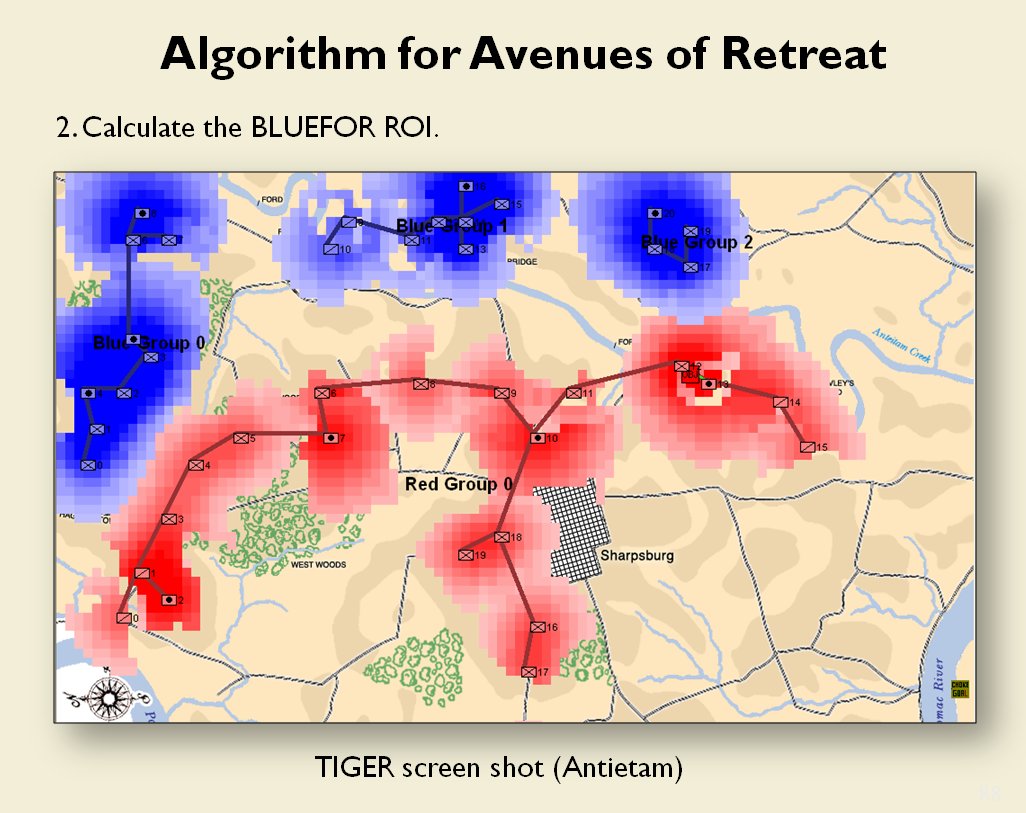
From the perspective of computer science restricted avenues of retreat and restricted avenues of attack are basically the same problem and can be solved with a similar algorithm.
As before we must first establish that there is agreement among Subject Matter Experts (SMEs) of the existence of – and the ability to quantify – the attributes of ‘Avenue of Attack’, ‘Avenue of Retreat’ and ‘Choke Point’.
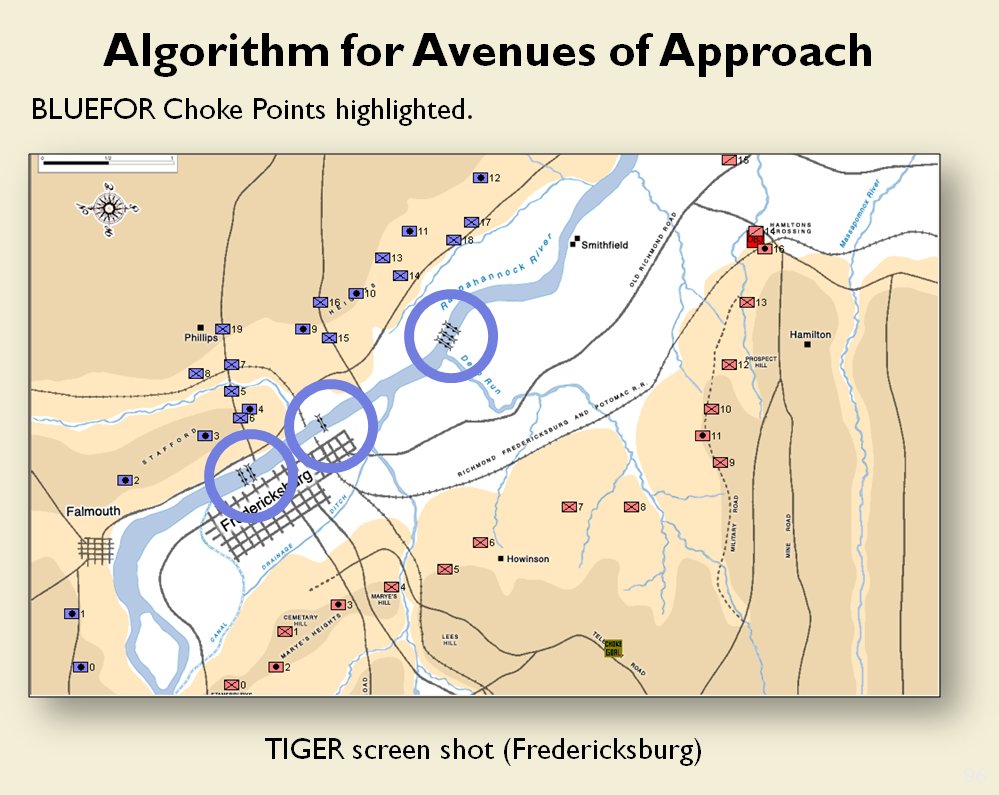
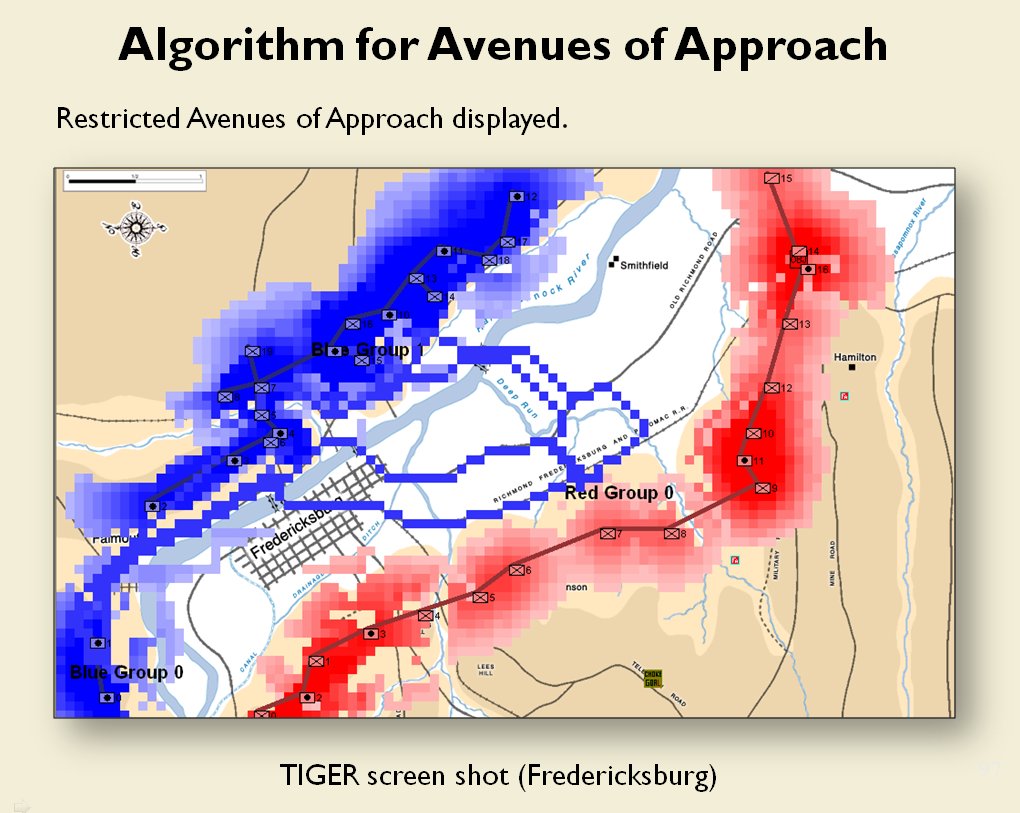
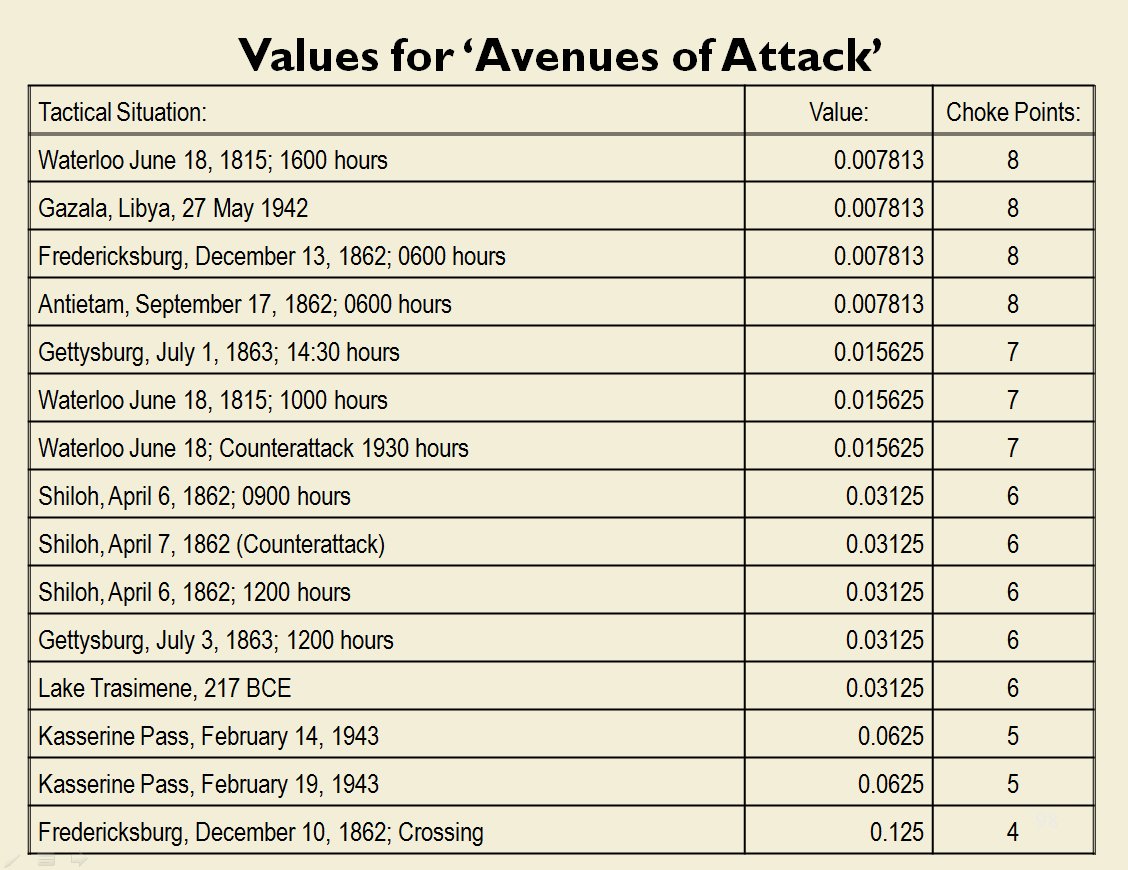
The following slides are from an unclassified briefing that I gave to DARPA (the Defense Advanced Research Project Agency) on my MATE program (funded by DARPA research grant W911NF-11-200024):
All slides can be enlarged by clicking on them.
Now that we have determined if there is a restricted avenue of attack the next blog post will discuss what to do with this information; specifically the implementation of the infiltration and penetration offensive maneuvers.
As always, if you have any questions please feel free to email me.
References:
TIGER: An Unsupervised Machine Learning Tactical Inference Generator, Sidran, D. E. Download here.