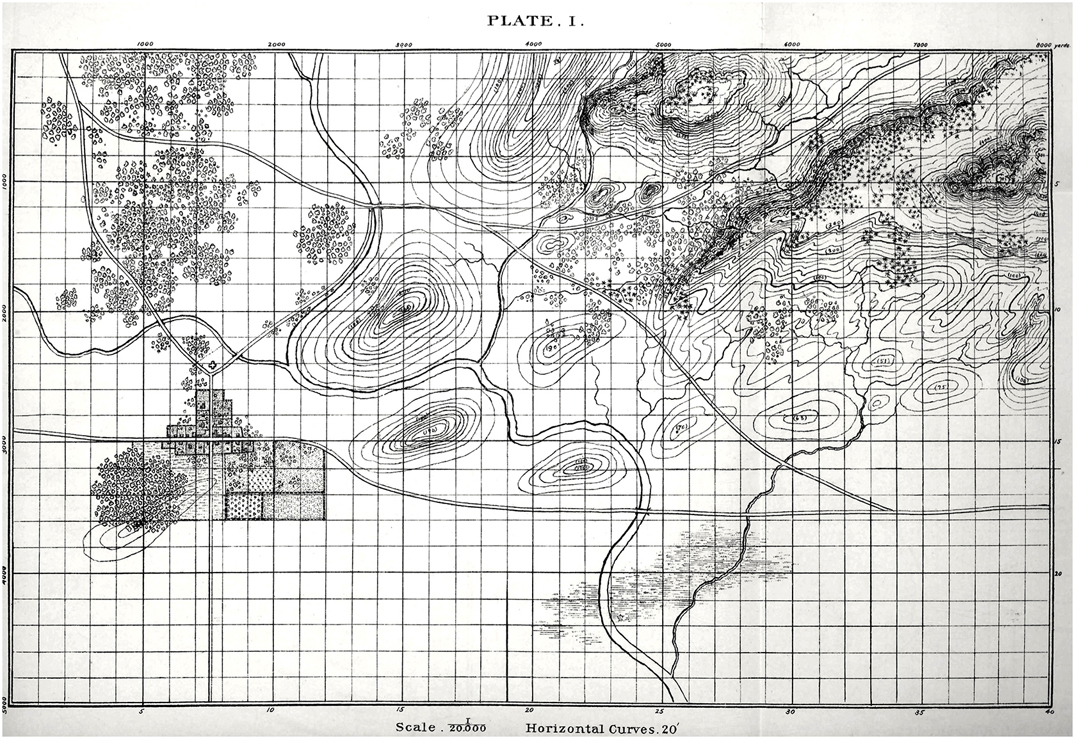
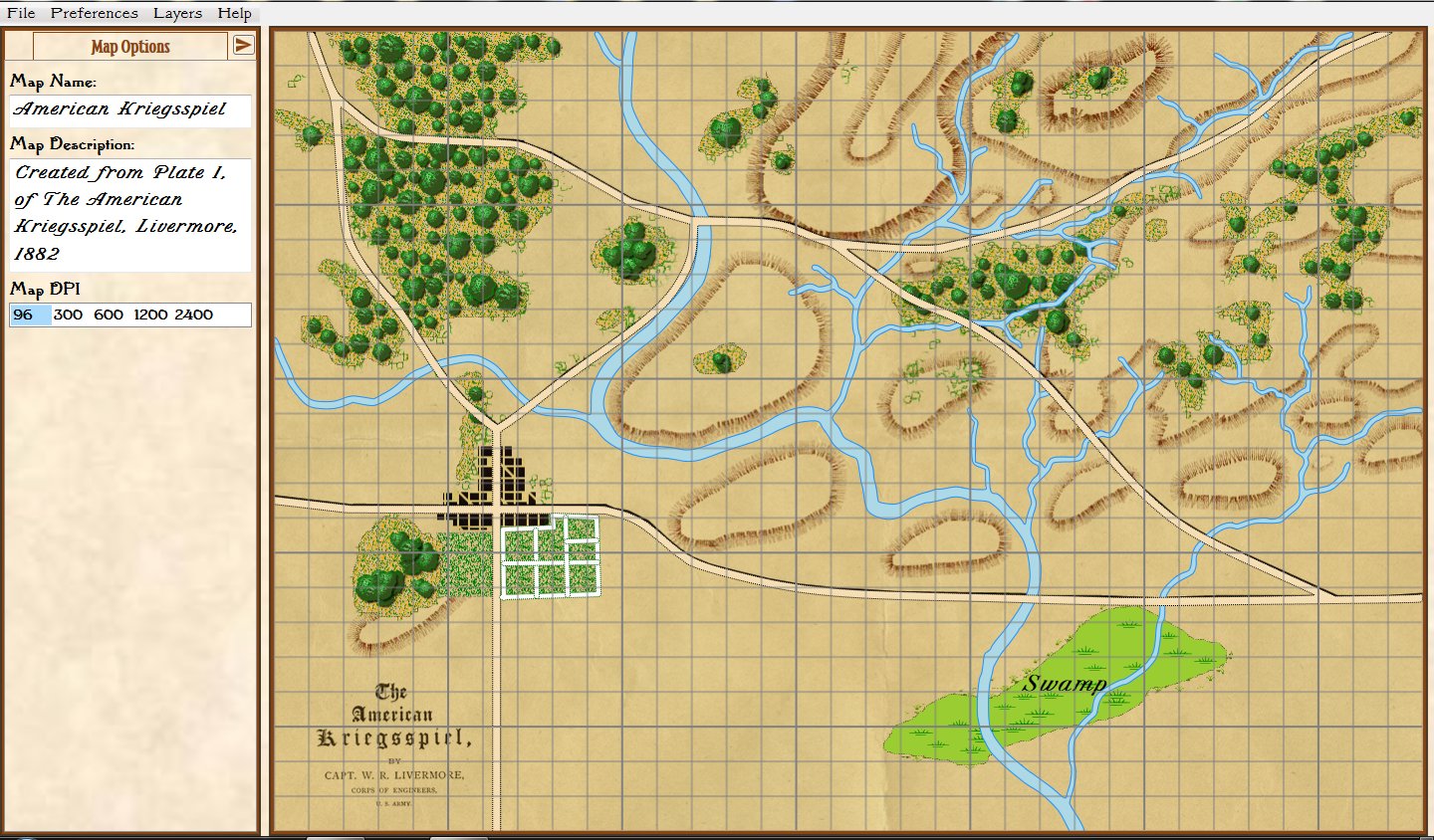
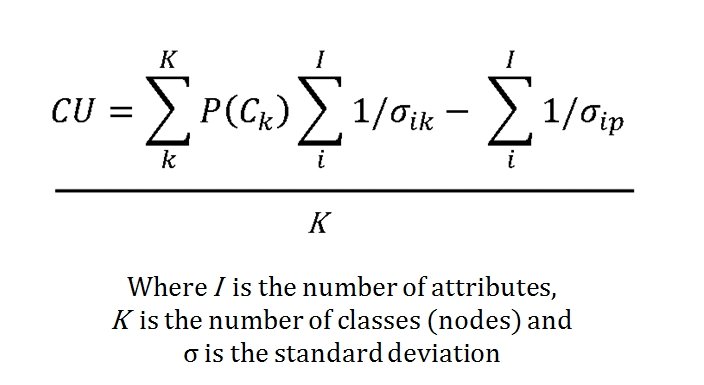
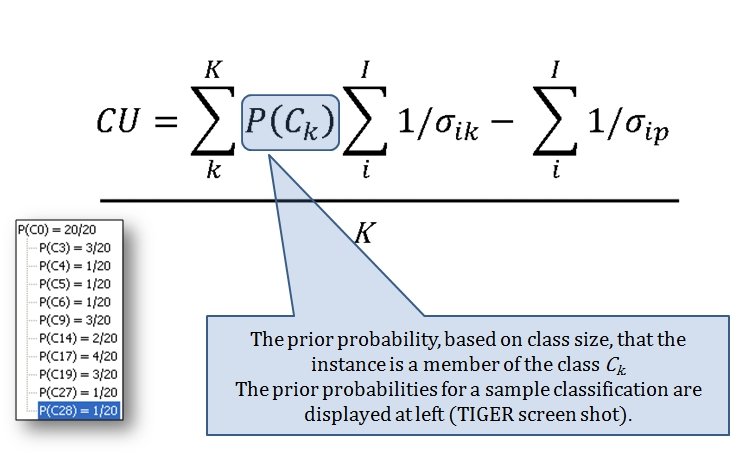
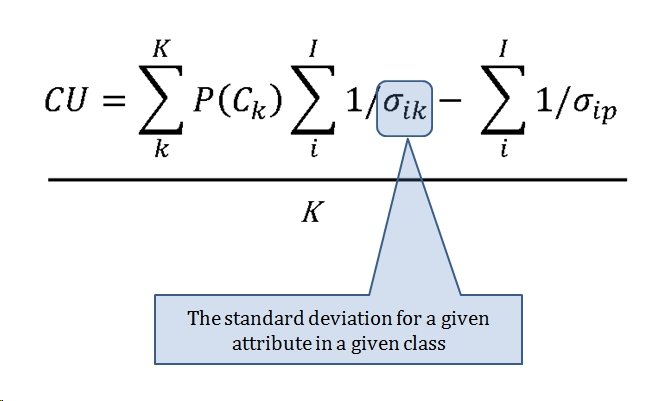
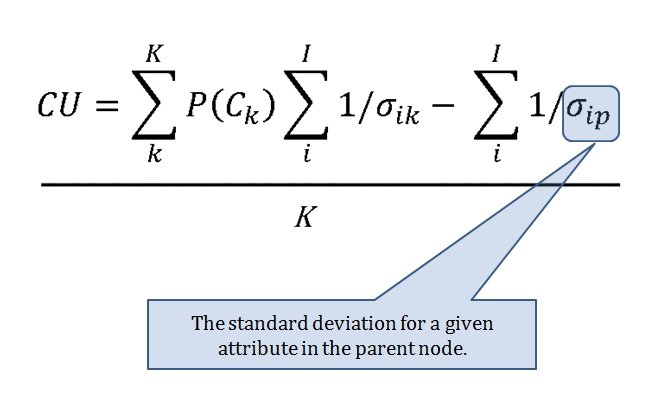
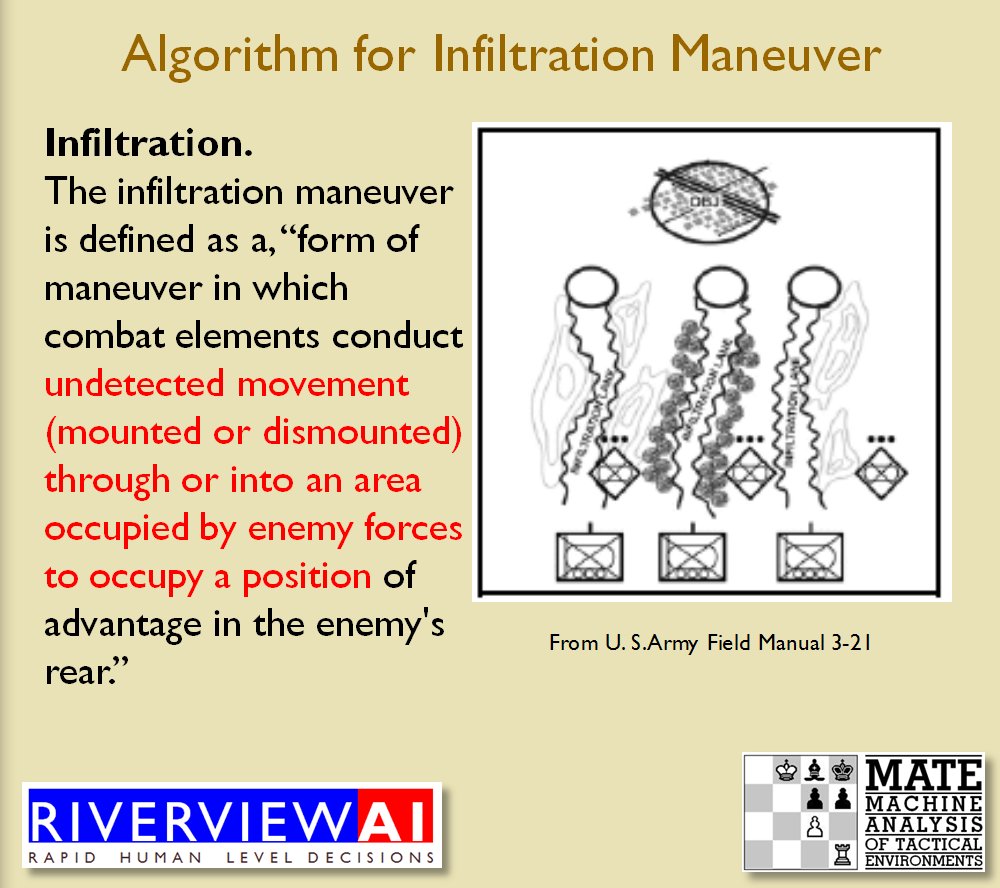
I‘m used to learning a lot when researching a battle but nothing prepared me for the ‘what ifs’ of Little Bighorn. My doctorate is in computer science but I have been an American Civil War buff since I was about five years old. I’m very familiar with brevet Major General George Armstrong Custer’s achievements during the Appomattox campaign where he commanded a division that smashed Pickett’s right flank at Five Forks. I knew that after the war Custer returned to his previous rank in the U. S. Army of Lt. Colonel, that he fell under a cloud with U. S. Grant, was stripped of his command, and had to beg for it back from President Grant, himself, at the White House.

Brevet Major General George Armstrong Custer taken May 1865. Credit: Civil war photographs, 1861-1865, Library of Congress, Prints and Photographs Division. Click to enlarge.
And, of course, I knew of the debacle at the Little Bighorn.
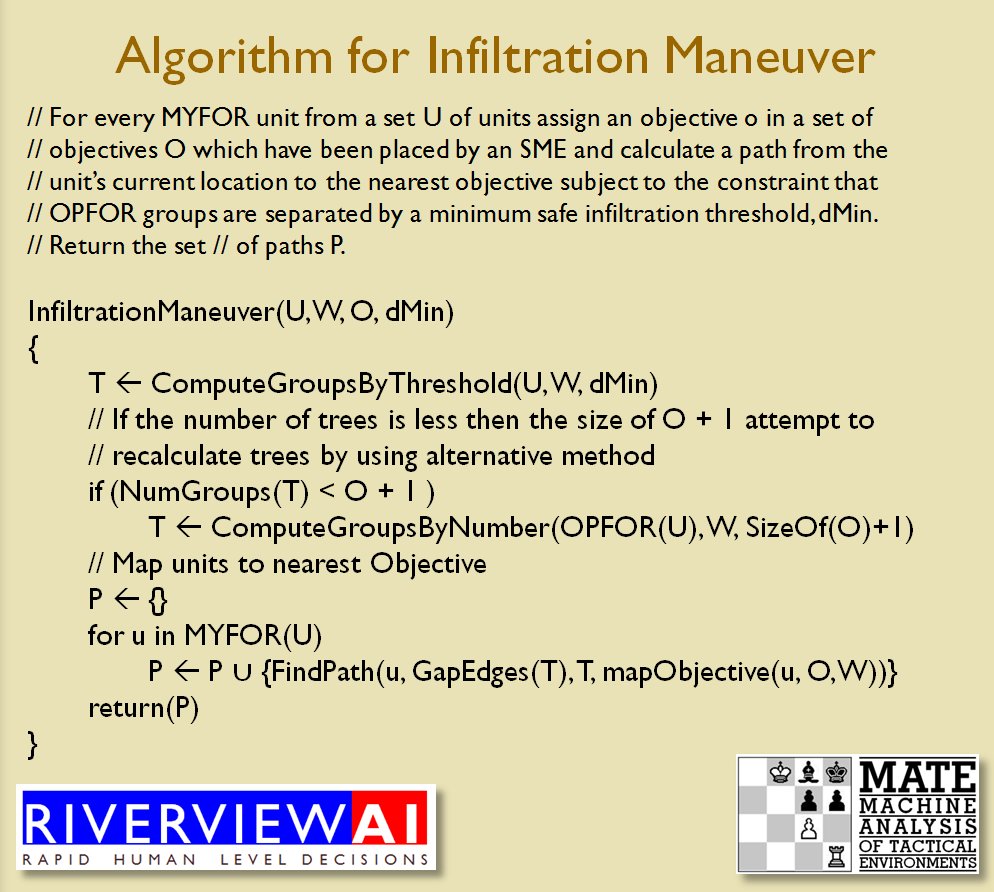
After I wrote UMS, the first computer wargame construction system, users began to send me Little Bighorn scenarios that included Gatling guns. I assumed that these were science fiction ‘what if’ scenarios. such as a story I read back in the ’60s about what if Civil War units had automatic weapons from the future. But, recently, while reading Stephen Ambrose’s Crazy Horse and Custer I learned that General Alfred Terry, Custer’s superior and the commander of the expedition, had indeed offered Custer not just three Gatling Guns (manned by troops from the 20th Infantry 1)The Guns Custer Left Behind; Historynet
https://www.historynet.com/guns-custer-left-behind-burden.htm ) but four extra troops from the 2nd U. S. Cavalry. Custer turned down Terry’s offer of reinforcements and more firepower with these infamous words:
“The Seventh can handle anything it meets.” – Custer to Terry

Photo taken by F. Jay Haynes of one of the Gatling guns that were available to the 7th Cavalry. Click to enlarge.
Screen capture of the Order of Battle of the 7th US Cavalry with the addition of 3 Gatling guns and 4 companies of the 2nd US Cavalry. Click to enlarge.
As for the battle of Little Bighorn, itself, I didn’t know much more than the broad outline that Custer and his command were killed to the last man by an overwhelming number of Native American warriors (this, of course, wasn’t correct as members of Reno’s and Benteen’s columns survived). Custer, himself, was the text book image of hubris and became the butt of late night comedians and humorous pop songs. But the reality turned out to be much more complex and nuanced.
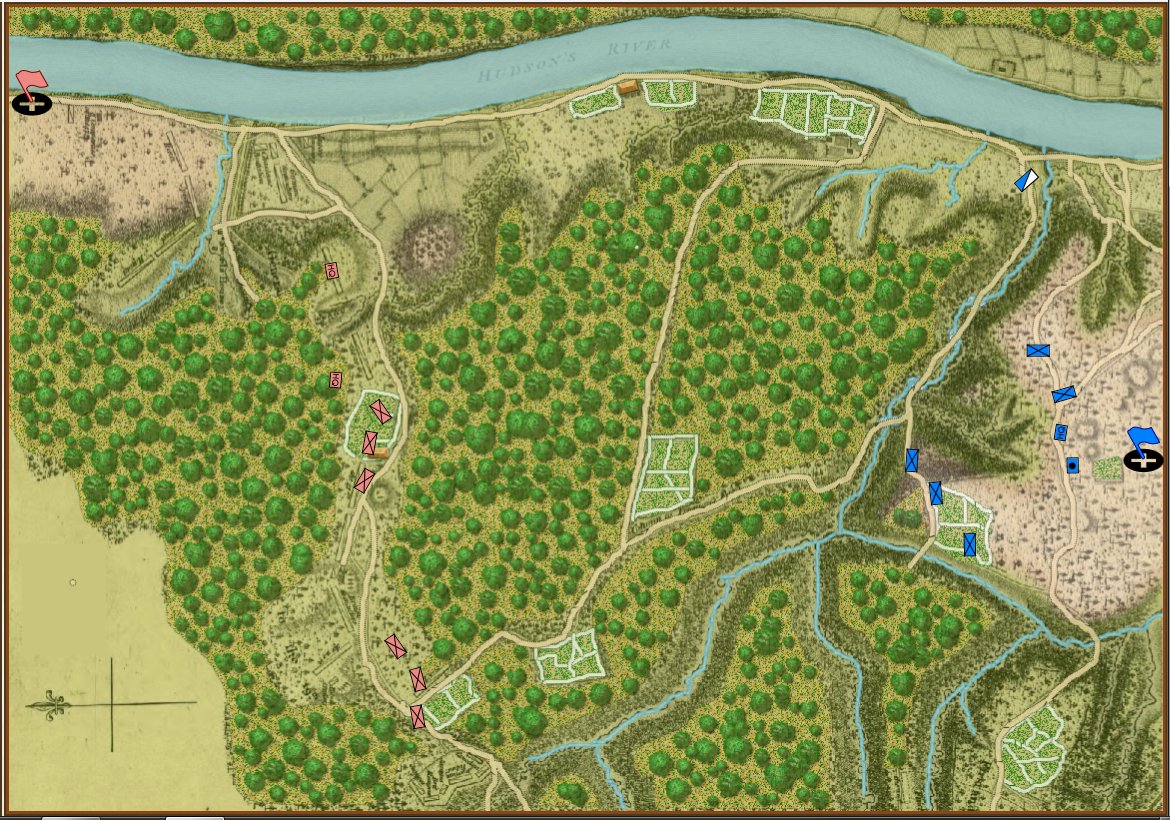
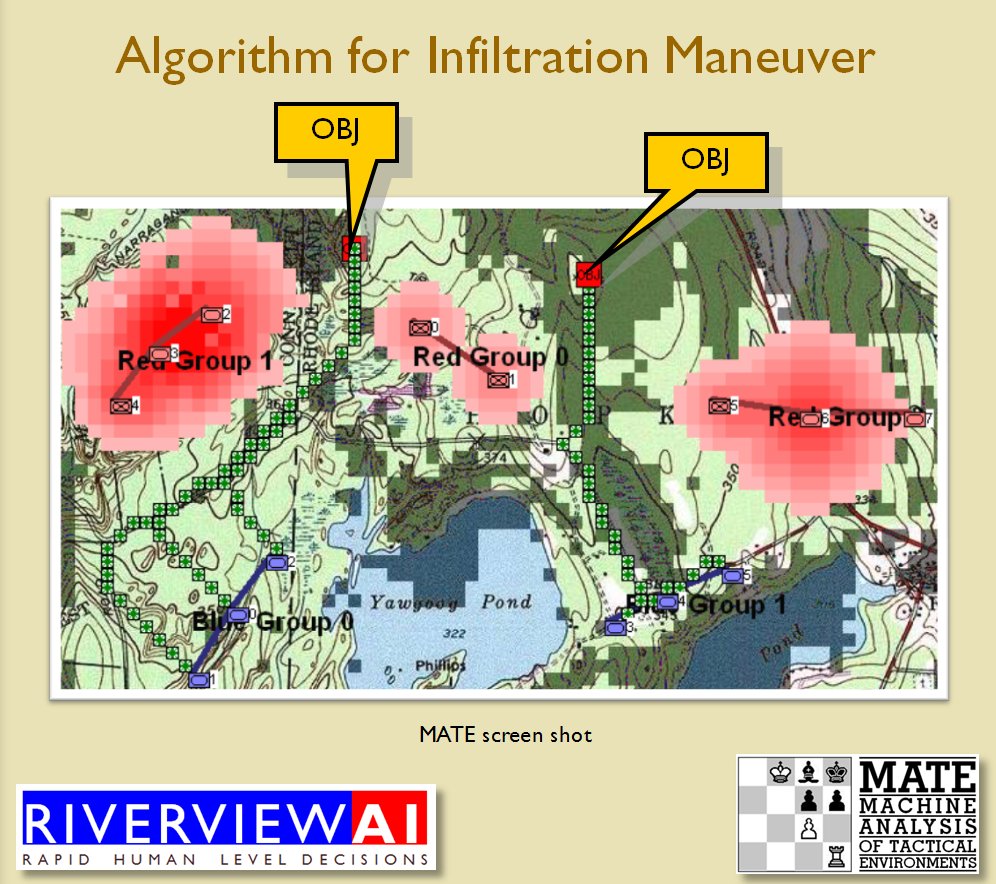
Custer had a reputation of being dashing, headstrong, and gallant; the iconic description of a cavalry commander. The traditional narrative of the disastrous battle of Little Bighorn is that Custer impulsively attacked a vastly superior enemy force; possibly propelled by a belief that Native American warriors were no match for organized cavalry armed with 45-70 trap door carbines. Indeed, Napoleon’s maxim was that, “twenty or more European soldiers armed with the best weapons could take on fifty or even a hundred natives, because of European discipline, training and fire control.” 2)“Crazy Horse and Custer” p. 425 Stephen Ambrose To make matters worse, Custer had pushed the 7th mercilessly and by the time they arrived at the battlefield both men and horses were exhausted.
Custer’s plan of attack is also widely condemned as overly optimistic. He split his command of 616 officers and enlisted men of the 7th cavalry into three battalions. If the four companies of 2nd Cavalry had come along, Custer’s force would be 30% larger.3)Ibid The main force led by himself would be the right flanking column, Reno would have the left flanking attack column and Benteen and the pack train would be in the middle. Custer also drastically underestimated the Native American force at about 1,500.
In theory, Custer’s plan of attack wasn’t that bad:
- If Custer was up against a force that was only two or three times his size and
- If Reno had pressed home his attack drawing the Native American warriors east toward him and
- If Custer had been able to cross the Little Bighorn above the Native American camp and
- If Custer had been able to attack the village while the warriors were engaged with Reno
Custer might have, indeed, had a great victory that would have propelled him to the US Presidency (as he had hoped). But none of these suppositions were correct.
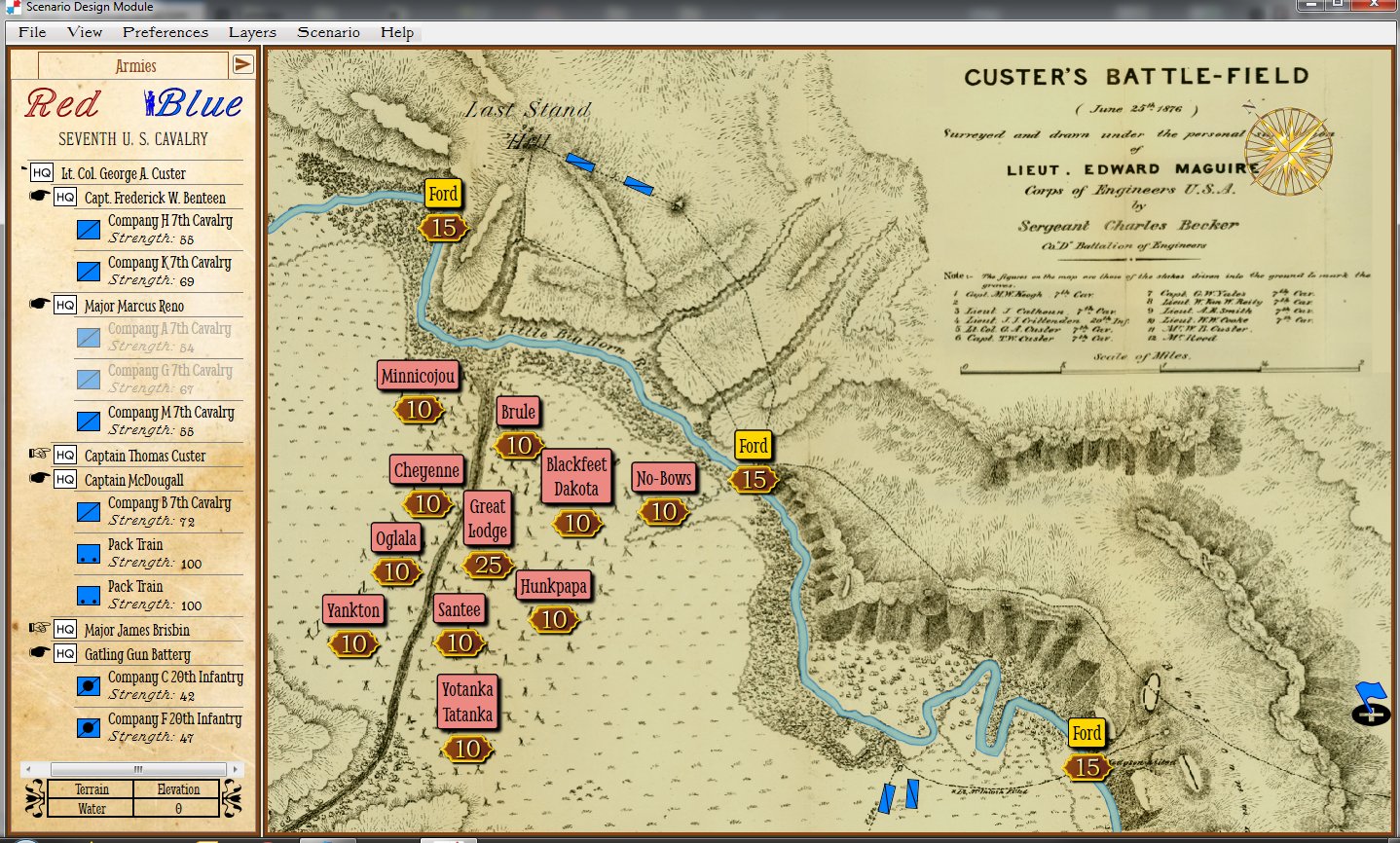
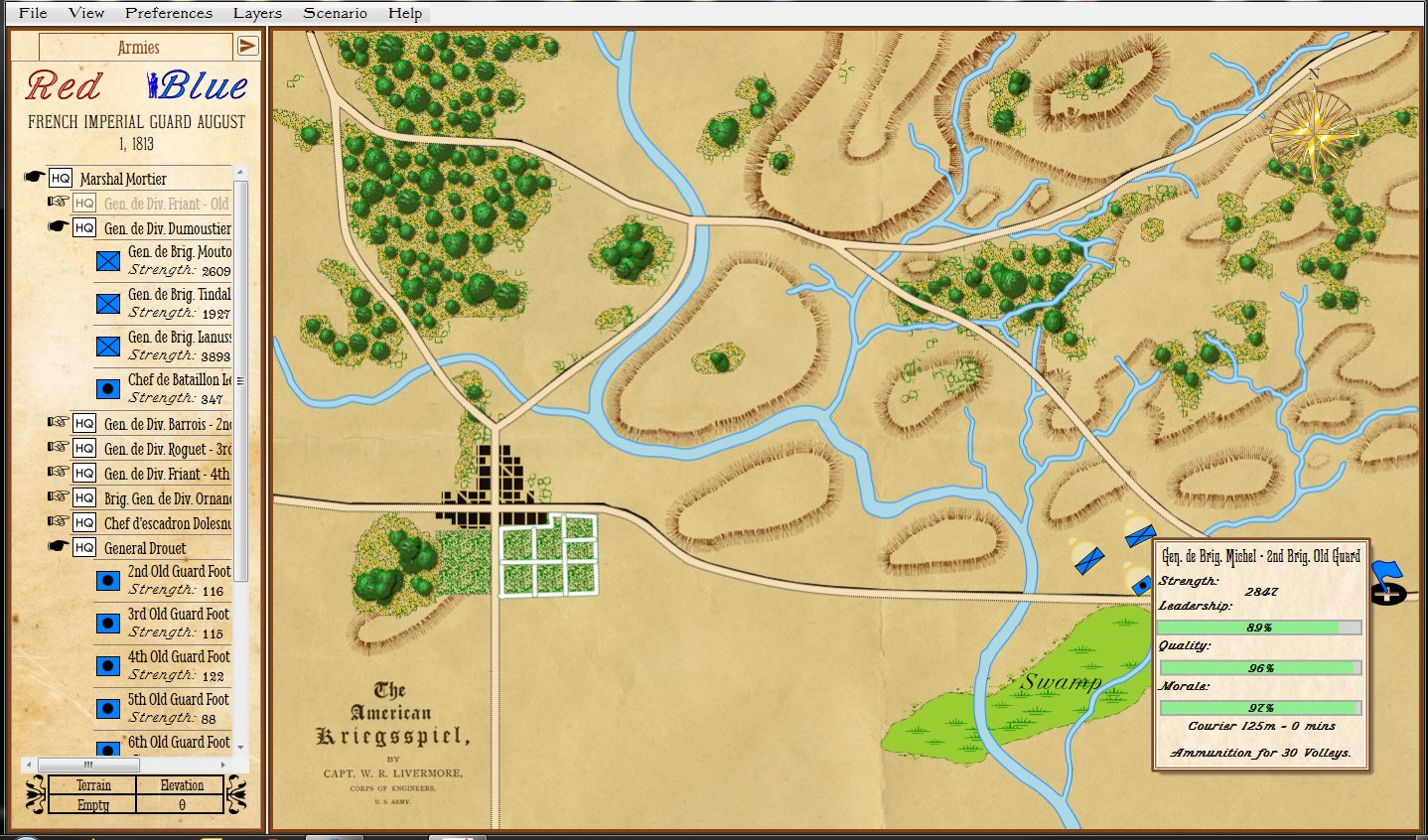
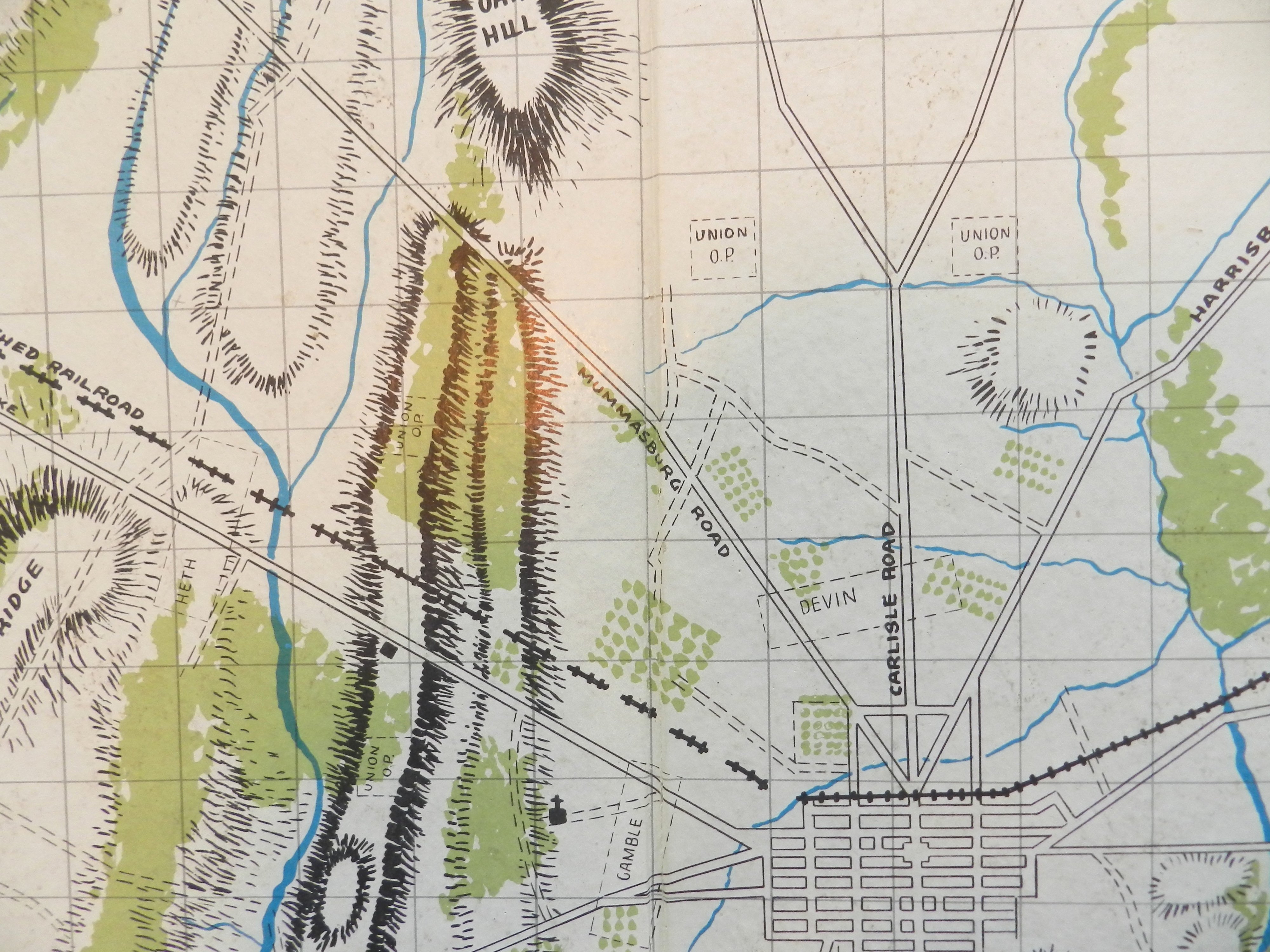
Screen shot of the General Staff Scenario Editor where the battle of Little Bighorn scenario is being set up. Not the Order of Battle of the 7th Cavalry (with attached units of the 2nd Cavalry and Gatling guns) on the left. Units are positioned by clicking and dragging them from the Order of Battle Table on the left onto the map. Click to enlarge.
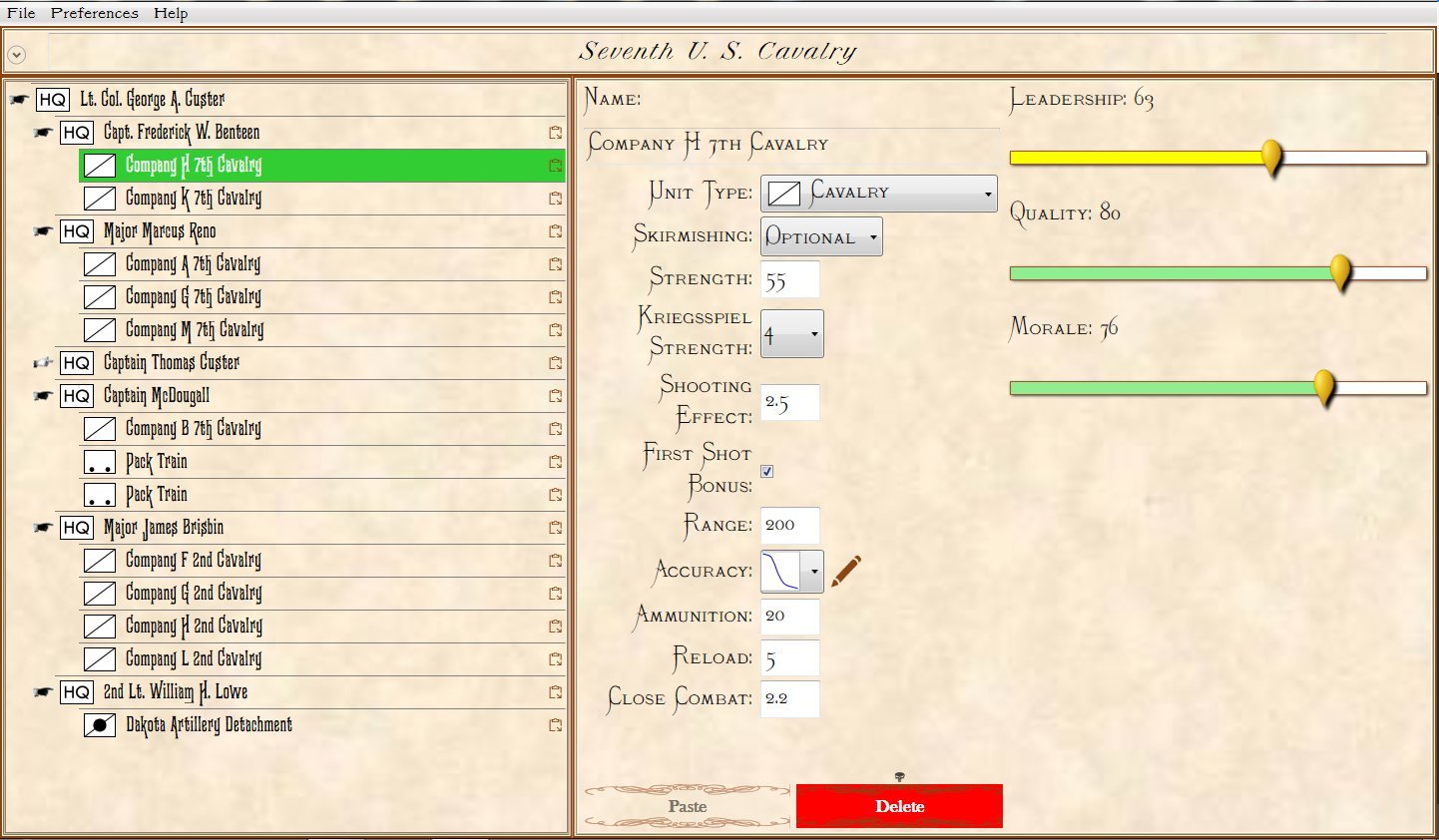
So, the question remains: what value for Leadership would you give to Custer?

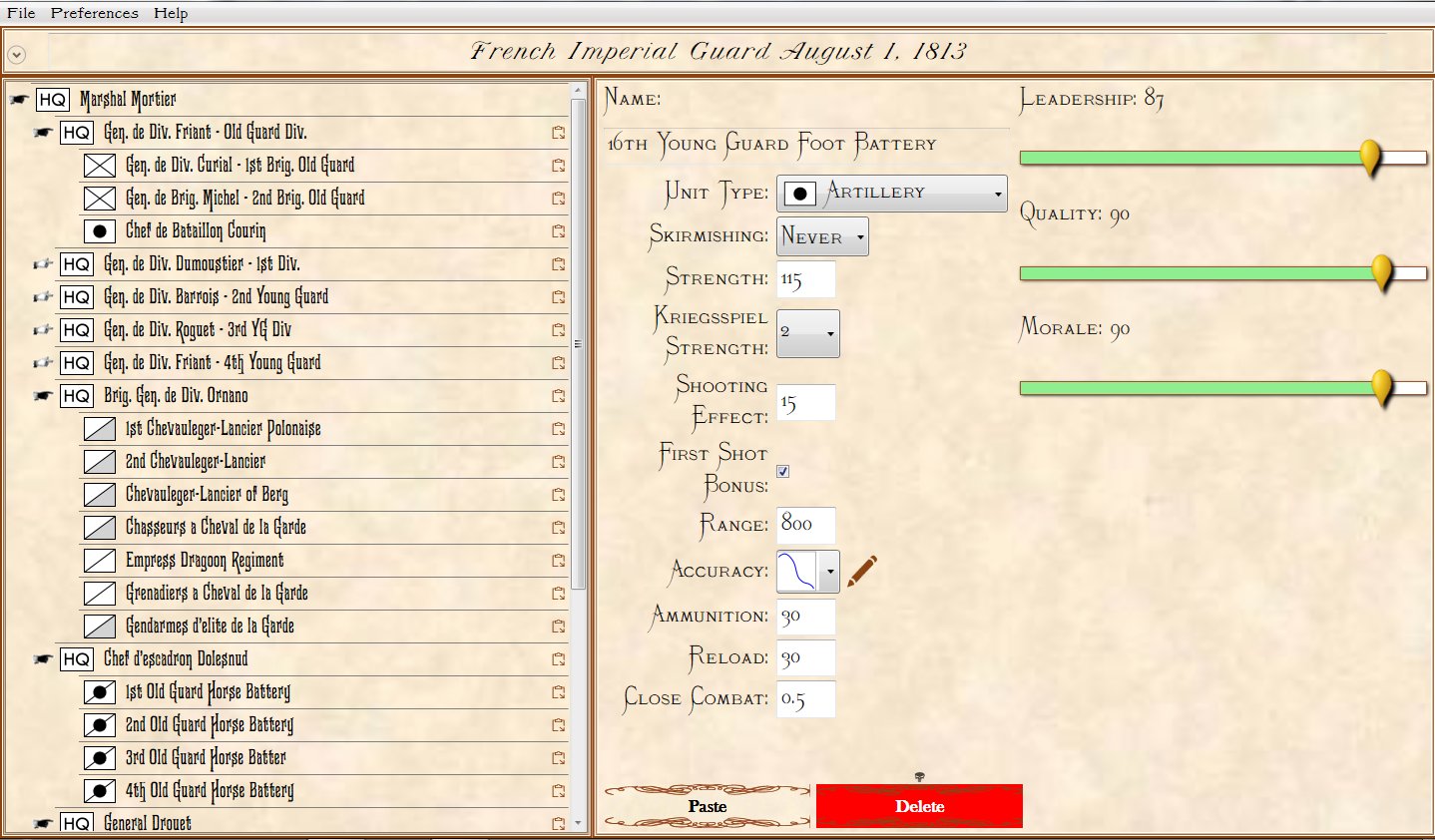
Screen shot of the General Staff Army Editor showing the slider that sets the Leadership value for a commander. What value would you give Custer? Click to enlarge
By the way, there will be three separate Little Bighorn scenarios for the General Staff Wargaming System: historically accurate Order of Battle for the 7th Cavalry, the 7th Cavalry plus four companies of the 2nd US Cavalry and 7th Cavalry plus four companies of the 2nd US Cavalry and 3 Gatling guns.
References
| ↑1 | The Guns Custer Left Behind; Historynet https://www.historynet.com/guns-custer-left-behind-burden.htm |
|---|---|
| ↑2 | “Crazy Horse and Custer” p. 425 Stephen Ambrose |
| ↑3 | Ibid |